This is why we can't have nice things
Don't start multiple threads about the botnet topic. They will be deleted.
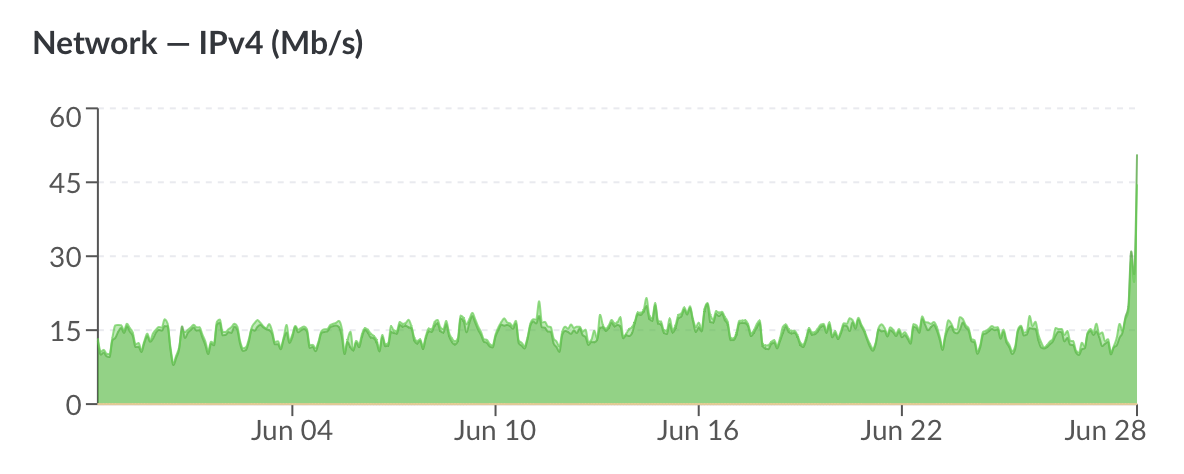
The proxy service has been disabled because the money (for which I am not compensated) is now flying out of my back pocket:
I will try and develop a fix in the code to better identify and remove these connections.
Update: The proxy service has been re-enabled if you're running v1.690 or later.




Comments
v1.689 (and later) has countermeasures against the "botnet".
v1.690 (and later) is necessary for your Kiwi to resume using the proxy service.
These updates will happen automatically overnight (local time) unless you've disabled automatic updates. You can manually update by going to the admin page "update" tab and clicking "build now" and waiting 30 minutes or so for the build to complete. Your Kiwi will restart when the build is complete.
Thanks for what you do to support KiwiSDR.
That seems to work, they get kicked after 1-2 seconds. Thanks!
@jks was that traffic increase all from these HFDL bots?
Was that traffic increase all from these HFDL bots?
Don't know for sure of course, but that's the presumption.
As mentioned by @HB9TMC the botnet will still attempt to connect to your Kiwi, and will still be logged. But is now kicked within a few seconds which will cause much less harm.
So if you're running v1.689 or later and still see these log messages don't be alarmed. The countermeasure is working as intended. At some point maybe I'll stop logging the messages. But at this point they are useful because they tell us if the botnet has changed behavior.
A casualty is that it's now not possible to do TDoA near the HFDL frequencies, as someone just tried.
But yeah, that's why whe can't have nice things. Perhaps it's possible to have a whilte-list for the TDoA server. Or they'll give up soon and the filter can be removed.
I can change that. But we shouldn't be talking about specifics of the countermeasures here because, well, you never know who's reading..
On my test Kiwi in Europe it seems the bot may have stopped about 10 hours ago (it's now 18:55 UTC 30 Jun). This output is from running this command in the admin console:
msl | grs LEAVING | gr kiwi_nc | tail -n 10And the proxy service has returned to normal more or less:
They still tried it 2 hours ago here. From 11:49 to 11:54 and 17:11 to 17:17 UTC
A non-public security forum would be good perhaps.
Like I have time to setup and manage such a thing, lol
I do, I could set up a mailing list, if there is interest.
In case the botnet is using the rx.kiwisdr.com list as the source of public Kiwi IP addresses I have removed any Kiwis from that list that are not running v1.690 or later. Currently that is about 90 Kiwis (out of 750+ total).
These Kiwis did not update automatically overnight so must be set for manual updates.
I would like to know the IP addresses associated with the Kiwi log message
fingerprint-2 was denied connection. Note-2, not-3. The IP will appear in the LEAVING message just after.Do not post here. Email to support@kiwisdr.com instead. Thank you very much.
An easy way to do this is to use the following command in the admin console tab:
gr -A 1 fingerprint-2 /var/log/user.logGrrrr..
If - say for example, your router / firewall that fronts the proxy traffic is say a mikrotik, you should be able to create dynamic address lists, which get updated when detecting certain types of traffic, then dropping it at the edge using a relevant firewall rule - this will prevent this traffic from getting to your core network.
I found an interesting article from 2016 that uses a combination python script and a mikrotik router to detect and block botnet traffic.
There are several ways to skin this cat.
And the better part of a day wasted beefing up the kiwisdr.com filtering against this nonsense. Time I really need to be spending on the cool stuff that's coming..
rx.kiwisdr.com (aka kiwisdr.com/public) is now subject to a simple click/tap captcha to help evade recent DDoS attacks on kiwisdr.com.
Apologies, but this is the sorry state of the world we live in..
Do you mean the DDoS attacks on May 9th, like in the screenshot above?
Yes and no. There are all different kinds going on now.
I understood. Thanks!
That's a fairly elegant solution rather than a captcha, and it's in keeping with the current way to log into a Kiwi, and I thought it was just a new feature / UX upgrade! lol.... :-)
Well, let's see how long it remains effective.
Bookmarks with query strings: For those of you that have bookmarks to rx.kiwisdr.com or kiwisdr.com/public, those should carryover through the captcha and be applied. Please let me know if this doesn't seem to be working for you.
Examples:
rx.kiwisdr.com/?s=uk,gps
kiwisdr.com/public/?n=40
Clicking on these two links goes through the captcha and produces the desired results.
Is the traffic generated by web scraping bots? Would software like Anubis help with that?
I have no way of knowing. How could I? However the traffic pattern makes me think it is malicious. Already it has stopped. Which tends to indicate there is a human actively monitoring it. It also means they will probably try something else. But that is all speculation on my part.
What ever is either doing the routing and / or proxying should be logging the header information on what the traffic is. It would look quite obvious what the malicious traffic looks like.
I have the web server log and that's all I need. tcpdump when anything more specific required.
I'm not going to continue talking about this since we don't know who's reading the forum.
And there went half my day. This is from the forum server. Goddamn Chinese AI companies. OpenAI.com too (although they were slightly better behaved). I had to beef up the IP filtering on the forum server to match what the proxy/web server (kiwisdr.com) has.